What makes us different?
Our content is not just videos, here you’ll find explanations, tables, and useful additional material for the learning process and your daily job.
Permanent update: Most of the platforms are updated every six months or annually, Cybersecurity is totally dynamic and that is how your learning should be.
Access to Webinars and Events: For our students we create Monthly Update Spaces on relevant topics where we make demonstrations, share experiences, and resolve concerns.
Real World Practice: Our courses are oriented to the labor/productive market; we teach with real examples that you can face in your day to day life.
Here you can find
Red Team
The red team is responsible for conducting simulated cyberattacks and security assessments to evaluate and enhance the security posture of an organization. Comprised of skilled professionals, the red team mimics the tactics, techniques, and procedures of real-world attackers to identify vulnerabilities and weaknesses in systems, networks, and defenses. Through red team exercises, organizations can improve their cybersecurity defenses, incident response capabilities, and overall resilience to cyber threats.
Blue Team
The blue team is responsible for defending an organization’s systems, networks, and data against cyberattacks. Comprising cybersecurity professionals, the blue team monitors, detects, and responds to security incidents, working to prevent and mitigate potential threats. Through proactive security measures and collaboration with the red team, the blue team aims to maintain the integrity, confidentiality, and availability of the organization’s information assets.

Learners
0
Certifications
0
Courses
0
Subjects
0
Knowledge Change Your Reality
Hi, Welcome back!
Don't wait to learn!
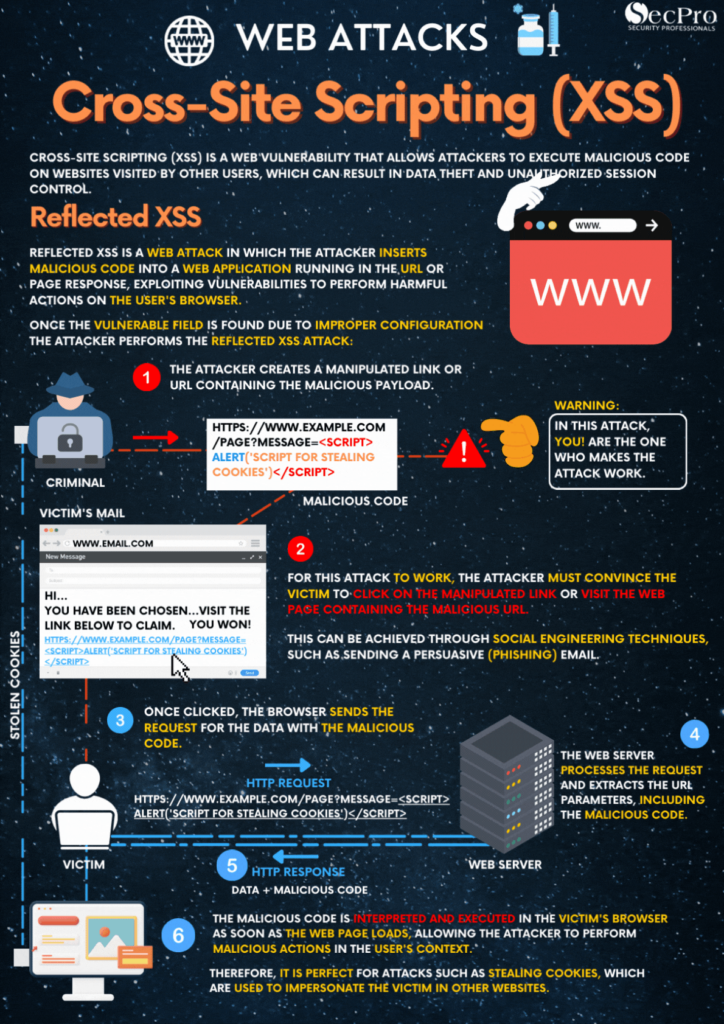
With us you will be able to learn several skills which are useful and demanded by the market, in addition to our courses you can access to Free Infographics in our other websites… Do you want to check more infographics? Just click Here